
Google has hosted a malicious advertisement that is so convincing, it has potentially deceived even the most security-conscious users who encountered it.
Complete Guide to Google Find My Device: All Your Questions AnsweredA screenshot of the ad reveals its deceptive nature:
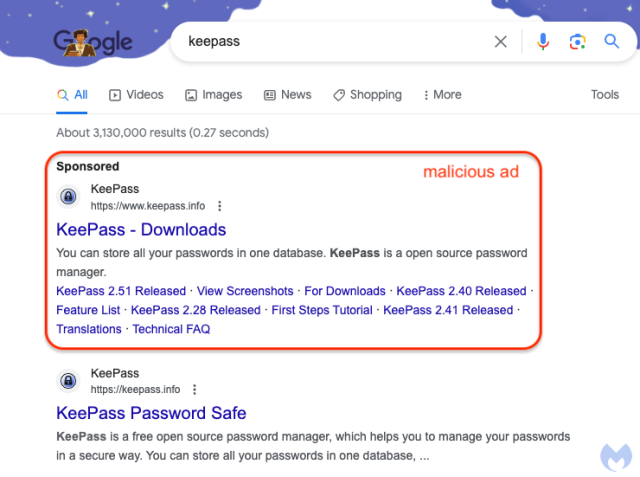
Source: Malwarebytes
 Safari Technology Preview 181: Apple unveils comprehensive details
Safari Technology Preview 181: Apple unveils comprehensive detailsUpon closer examination, it becomes apparent that the associated website, identified as ķeepass[.]info in the address bar, is not the genuine Keepass site. In fact, ķeepass[.]info is a coded representation of xn--eepass-vbb[.]info, which is associated with a malware family known as FakeBat. The combination of the convincing Google ad and the nearly identical URL creates a powerful means of deception.
The Mechanics of the Scam
Jérôme Segura, Head of Threat Intelligence at security provider Malwarebytes, explains, "Users are first deceived via the Google ad that looks entirely legitimate and then again via a lookalike domain" (Malwarebytes). The scam was unveiled in a blog post by Malwarebytes that exposes the use of punycode to create a URL that appears legitimate.
Save 7% on the OLED Mario Red Edition of Nintendo Switch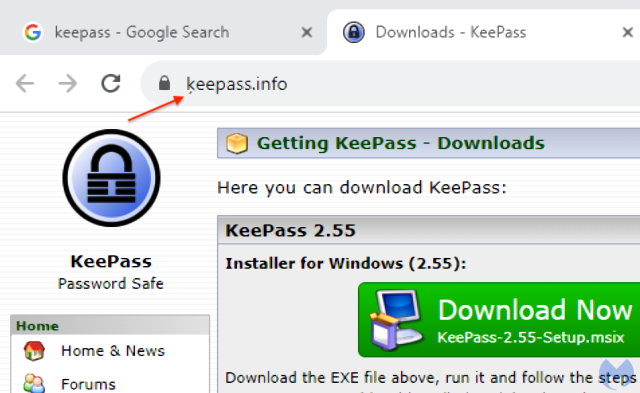
Source: Malwarebytes
Google's Ad Transparency Center reveals that the ads have been active since Saturday and were last seen on Wednesday. These ads were paid for by a verified advertiser called Digital Eagle.
OnePlus and BOE Unveil Revolutionary Smartphone Display with 3,000 Nits of Brightness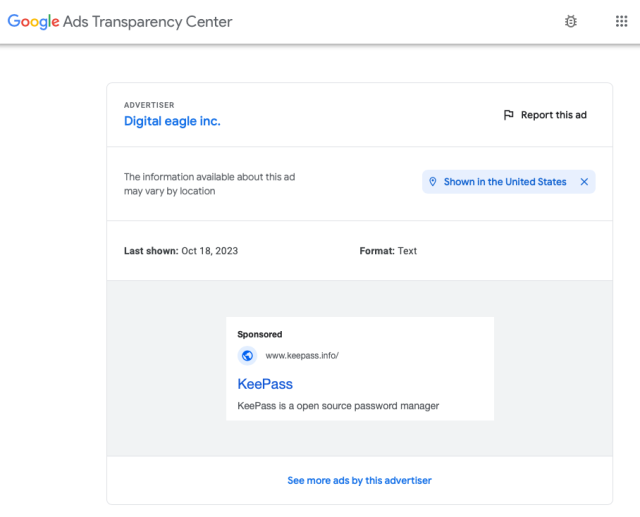
Source: Malwarebytes
Despite attempts to contact Google, the company has yet to respond. However, in previous cases, Google has stated that it promptly removes fraudulent ads once they have been reported.
 Xbox Achievements Revealed: Unveiling the Unstoppable Power
Xbox Achievements Revealed: Unveiling the Unstoppable PowerThe Power of Punycode
The technique used to make xn--eepass-vbb[.]info appear as ķeepass[.]info is known as punycode. This encoding scheme allows the representation of unicode characters in ASCII text. Careful inspection reveals a subtle difference in the URL, with a small, comma-like figure below the letter "k." This figure can be easily missed, especially paired with a valid TLS certificate.
Scammers have a history of utilizing punycode in their malicious schemes. Two years ago, a similar technique was employed to create a fake site resembling brave.com. This site aimed to deceive users into downloading a malicious version of the browser. The concept behind punycode gained attention in 2017 when a developer showcased a proof-of-concept website masquerading as apple.com.
Detecting both malicious Google ads and punycode-encoded URLs is challenging. Many major browsers do not distinguish between ķeepass[.]info and the imposter site. When uncertain, users can manually type the URL in a new browser tab or inspect the TLS certificate to verify its authenticity.

Leave a Reply